Vulnerability Research
Vulnerability Research – we will check your company’s vulnerability to cybersecurity incidents.
Analysis resistance to cybercriminal attacks is the first step to improving the security of any company. Our Vulnerability Testing Research allows for checking your company’s vulnerability to threats from the most popular input vectors. This is a very important research because it helps to avoid threats that affect the operation of the company and its ICT security.



Additional services
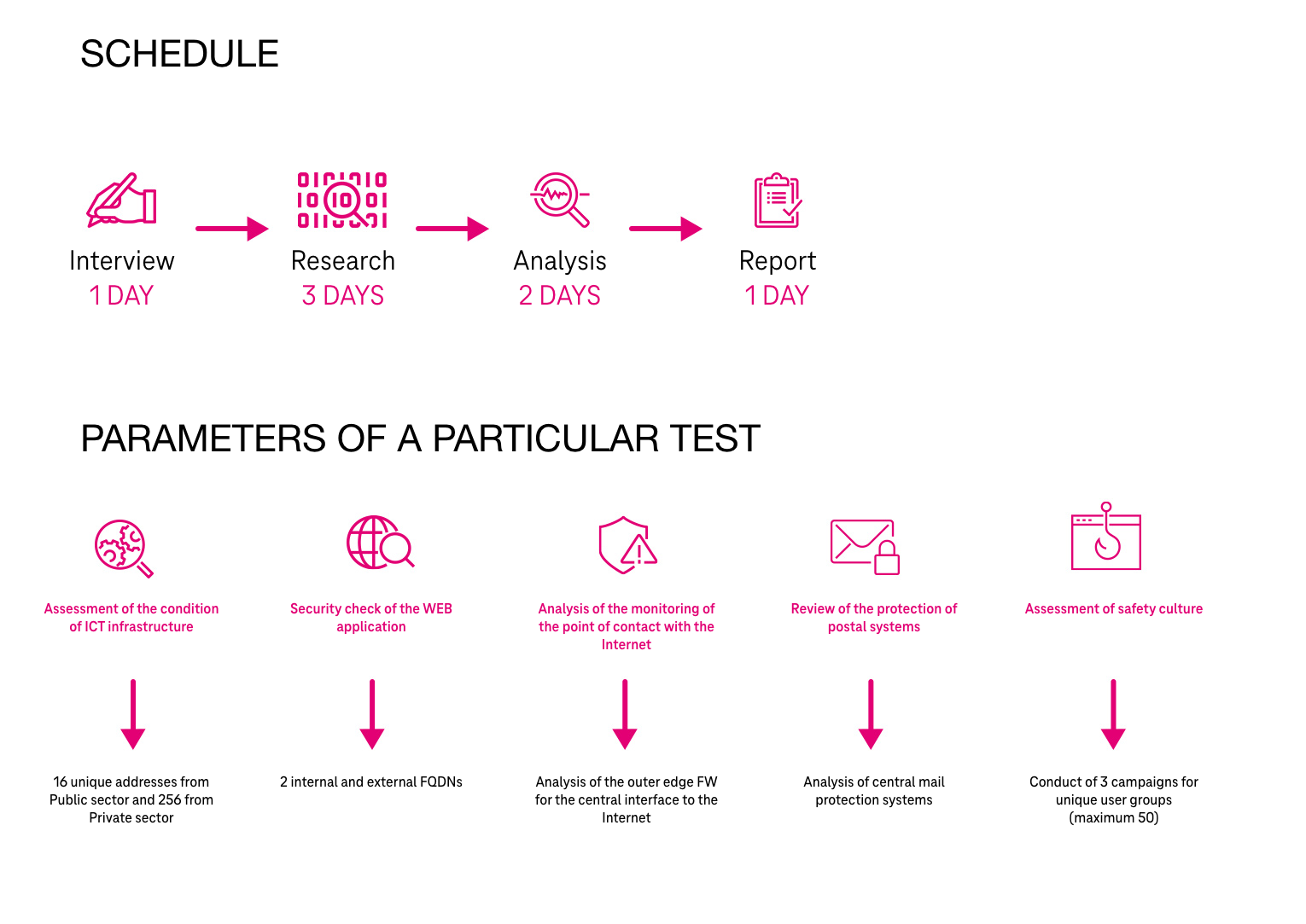
The Vulnerability Research offer is based on five levels:
-
ICT infrastructure vulnerability research:
1Identification and inventory of IT infrastructure resources. Demonstrating vulnerabilities, security gaps and configuration errors. Proactive action against identified threats, indicating the direction of corrective actions. Demonstrating the risks and critical areas that should be prioritized and eliminated.
-
WEB application vulnerability and security research:
2Active checking of vulnerabilities of WEB applications in terms of known vulnerabilities. Assessing the effectivness of WAF in detecting and blocking threats. Dynamic analysis of the application’s source code to identify programming errors. Identification of malware and content that can be embedded in WEB servers.
-
Analysis of supervision over the point of interconnection with the Internet
3Edge architecture analysis:
Verifying the ability to detect high-risk applications and content in the network traffic. IPS functionality check- detection and blocking of known exploit threats.
Detecting threats at the level of firewall functional modules.
-
Verification over the method of protecting e-mail systems:
4Identification of native protection mechanisms, policies and configuration of mail protection systems by generation special e-mail messages simulating popular attack techniques. Generating e-mail messages containing malicious URLs and attachments in order to verify their identifiability and blocking.
-
Assessment of the state of cyber security culture:
5Simulating real phishing campaigns. Non-invasive attacks targeted at selected groups of employees. Personalize the message content using dedicated templates.
How it works
Security
Awareness
We would like to present a service that will effectively improve the security of your company against cyber threats.
Unfortunately, human beings are still the weakest point of any security system. Most of the attacks are targeted at the company’s employees. According to information provided by ENISA, every third data leak is caused by phishing, and as much as 95% of malware reaches computers via e-mail. Security Awareness is a cyber threat awareness programme. How does it do it? By providing easy-to-understand interactive content to your employees, and simulating attacks, it checks and increases their vigilance.