Managed WAF
Secure eCommerce with a Managed WAF.
The Web Application Firewall (WAF) service is a solution dedicated to web application protection, enabling monitoring, filtering and control of http/https traffic.
Due to its attractive price, it is an ideal solution for eCommerce websites, where ensuring operational continuity not only enables order processing but also shows the company’s credibility.



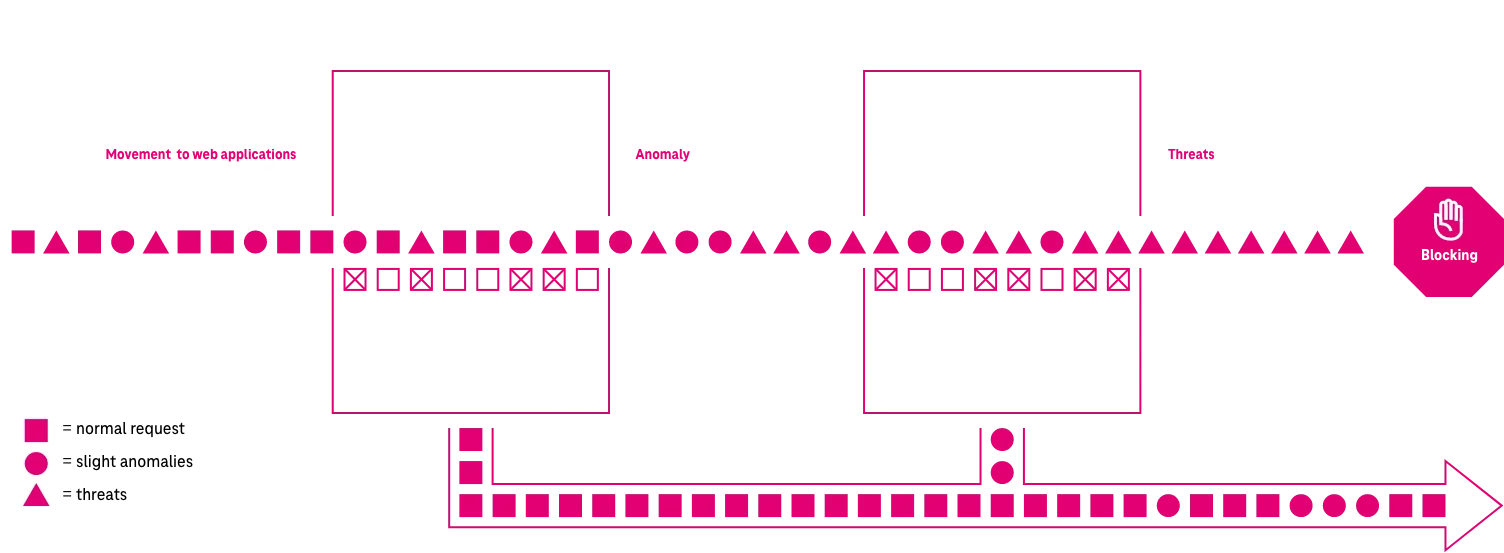
How it works
Comparison of packages
/month
Scope of service
-
Startup
The service is configured and launched based on the guidelines you specify (items to be whitelisted and blacklisted) and is tailored to the specifics of your sites.
-
Maintenance
The service is monitored and administered by T-Mobile’s SOC 24/7/365, and includes regular reporting and technical support.
-
Support
The service also includes backup of WAF configuration, log retention and a possibility to extend the service to monitoring and responding to incidents detected by WAF, as well as web application penetration tests.
Each of the stages is carried out by a qualified team of T-Mobile experts specializing in IT security
Technical
parameters
-
The fastest WAF on the market na rynku
Throughputs from 25Mbps to 20GBps
-
Vulnerability scanner
Built-in vulnerability scanner and integration with third-party scanners
-
Unique solution
Protection against SQL Injection, eliminating false positives and false negatives (based on SQL syntax, not signatures)
-
Protected bandwidth (to/from applications)
Up to 200Mbit/s
-
FortiView
Built-in visualization of all WAF components in one place, without the need to buy and install separate environments
-
Machine Learning
Innovative machine learning technology to minimize false positives.
-
Loadbalancing
L7-based content and SSL hardware acceleration.
-
Provisioning model
- Central (virtual machine created in T-Mobile Data Center and managed by SOC)
- Local (physical device installed in the client’s location, managed by VPN and SOC)
Protection against threats

The application firewall protects websites against attacks that use vulnerabilities described, among others, on the OWASP TOP 10 list.
These include:
-
Code injection.
-
Flawed authentication.
-
Exposure (compromise) of sensitive data.
-
Flaws in applications that parse XML files (XML eXternal Entity).
-
Errors in access control mechanisms.
-
Errors in security configurations.
-
Cross-Site Scripting (XSS).
-
Unsecured deserialization mechanisms.
-
Use of software containing known vulnerabilities.
-
Insufficient monitoring and logging.





