AntiDDoS
Guarantee of website availability thanks to Anti-DDoS.
Anti-DDoS service offered by T-Mobile is an uninterrupted protection of websites allowing to ensure their constant availability.
It consists in active network monitoring and quick reaction to block artificial traffic generated by botnet networks.
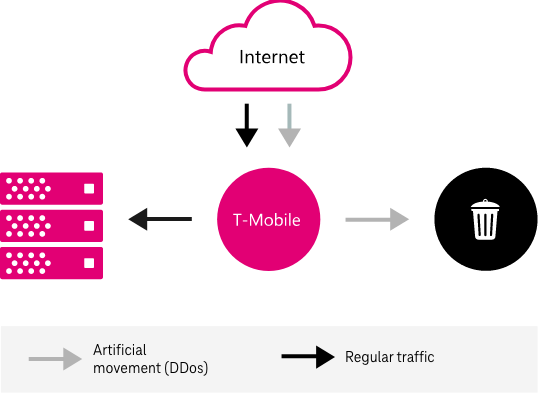

Scope of service
The offer of protection against DDoS attacks (Distributed Denial of Service) includes two elements of the service.
Comparison
of packages
-
Comparison
of packagesPackage
BronzePackage
SilverPackage
Gold -
SLA guarantee
-
Daily update of signatures
-
Service management by T-Mobile Polska
-
Client support center 24/7/365
-
Dedicated thresholds
alarm(based on customer data)
(established with the support of T-Mobile)
(established with the support of T-Mobile)
-
Dedicated mitigation profile
(based on customer data)
(established with the support of T-Mobile)
(established with the support of T-Mobile)
-
24/7/365 Layer 3 and 4 attack monitoring
-
Access to web-based information portal
informacyjnego(1 account)
(1 account)
(3 accounts)
-
Number of protected objects
1
1
Up to 3
-
Automated mitigation
-
Possibility of running the mitigation by the user
-
Execution time of protection procedure
Up to 30 minutes
Up to 30 minutes
Up to 30 minutes
-
Start time of protection (auto-mitigation)
< 1 minute
< 1 minute
< 1 minute
-
Informing about events (e-mail, SMS)
-
Tests of security procedures
optional
at startup
-
Platform availability
99,99%
99,99%
99,99%
AntiDDoS
protection process
-
Planning
1Development and implementation of a protection plan tailored to the Client’s needs.
-
Continuous monitoring
2Incoming and outgoing data flows along the usual, unchanged route. DDoS attack monitoring system continuously analyses received traffic, comparing its parameters with established threshold values and characteristics of historical incoming traffic
-
Attempted DDoS attack
3When the monitoring system detects a threat, it records it and immediately notifies the team and the Client via SMS and email. The SOC T0 Mobile expert immediately checks and classifies the incident and then contacts the Client to inform them of the situation.
-
Mitigation of a DDoS attack
4Classification of an event as a DDoS attack triggers the threat mitigation procedure. In less than a second, incoming traffic is redirected to T-Mobile’s traffic cleaning center (where so-called scrubbing takes place) and the client’s web application regains full availability. In order to achieve the most important standard of protection, T-Mobile technical staff will monitor the event as long as the stream of malicious traffic directed towards the Client’s network is detected.
-
End of DDoS attack
5Once the appropriate time indicators show that the traffic has returned to normal, T-Mobile’s expert will terminate the prevention porcedure and redirect the traffic to a normal path.
Technical
parameters
-
High performance platform
> 200 Gb/s.
-
Technology
Arbor Networks leading technology solutions.
-
Option
Application layer attack protection.
-
Redundancy
Secure and antiDDOS platform located in T-Mobile Data Center in Poland.
-
Individual protection plan




